Meet the Attack-Flow Graph for Every CVE Report
Publication date: 2025-08-14
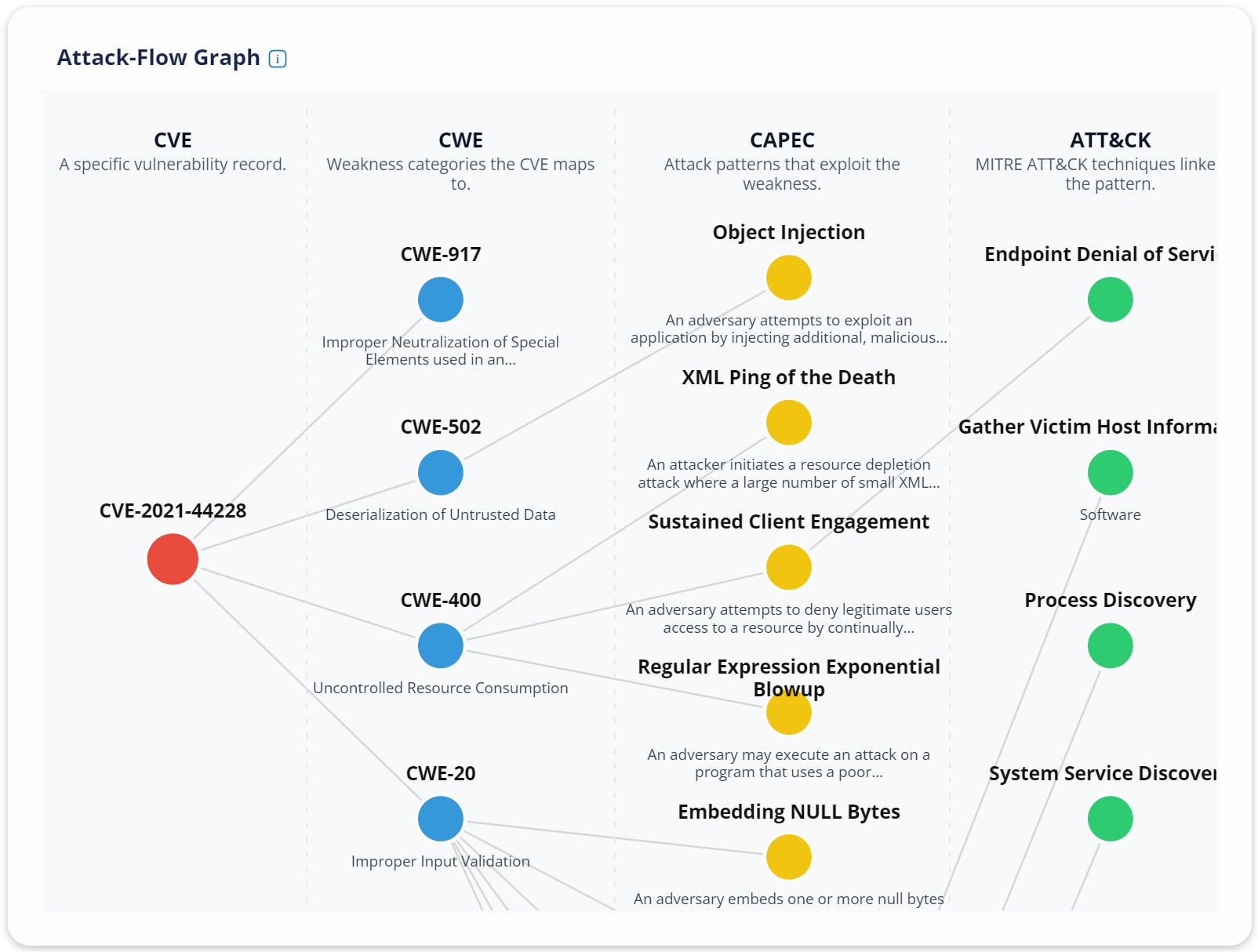
We’ve added a new visual to every CVE page on BaseFortify: the Attack-Flow Graph. It turns a vulnerability entry into a clear story of how that weakness can be exploited and what an attacker is likely to do next.
What it conveys
Most reports tell you what is vulnerable. The Attack-Flow Graph shows how a real attack could unfold:
- CVE → CWE → CAPEC → MITRE ATT&CK
Four vertical lanes trace the path from the specific CVE, to the underlying weakness (CWE), to known attack patterns (CAPEC), and finally to the adversary techniques you track in MITRE ATT&CK.
- Cause and consequence, side by side
Developers see the class of flaw that needs fixing; defenders see the techniques to watch for while patches roll out.
- Faster prioritization
When a CVE links to impactful patterns and high-signal ATT&CK techniques, you immediately understand potential blast radius and where to focus effort.
- Communicable risk
One picture explains the exploit path to non-specialists—useful for change boards, leadership updates, or customer notifications.
How to read it
- CVE (left): the vulnerability you’re viewing.
- CWE: the weakness category the CVE maps to.
- CAPEC: attack patterns that exploit that weakness.
- ATT&CK (right): techniques adversaries use when executing those patterns.
Nodes are colour-coded by lane; connecting lines show relationships. Hover to see full IDs and titles; scroll to zoom and drag to pan. Lane headings include short hints to remind you what each column represents.
Availability and access
The graph now appears on all CVE pages. Everyone sees the header and a soft preview; sign in (or register free) to explore the full interactive view.
Why it matters
Security decisions are easier when evidence is visual. The Attack-Flow Graph helps you:
- move from severity to exploit context;
- plan detections aligned to ATT&CK while remediation is in progress;
- coordinate Dev, Sec, and Ops around the same picture;
- explain risk and mitigation with clarity.
Popular CVEs to explore
If you’d like to see strong, clear examples of Attack-Flow Graphs in action, check out:
- CVE-2014-0160 – Heartbleed – A famous information disclosure flaw with direct credential access implications.
- CVE-2021-44228 – Log4Shell – A highly impactful case of input handling leading to remote code execution.
- CVE-2014-6271 – Shellshock – A concise injection path from vulnerability to command execution.
Resources
- MITRE ATT&CK
- MITRE CAPEC
- MITRE CWE
- NVD – National Vulnerability Database
- CISA Known Exploited Vulnerabilities
We’d love your feedback—tell us how the graph supports your workflow and where we can make it even more useful.
