BaseFortify Features
Explore the core functionality of our platform and see how it supports daily security work. Manage components with ease and keep visibility across your digital environment.
Clear, Focused Vulnerability Insights
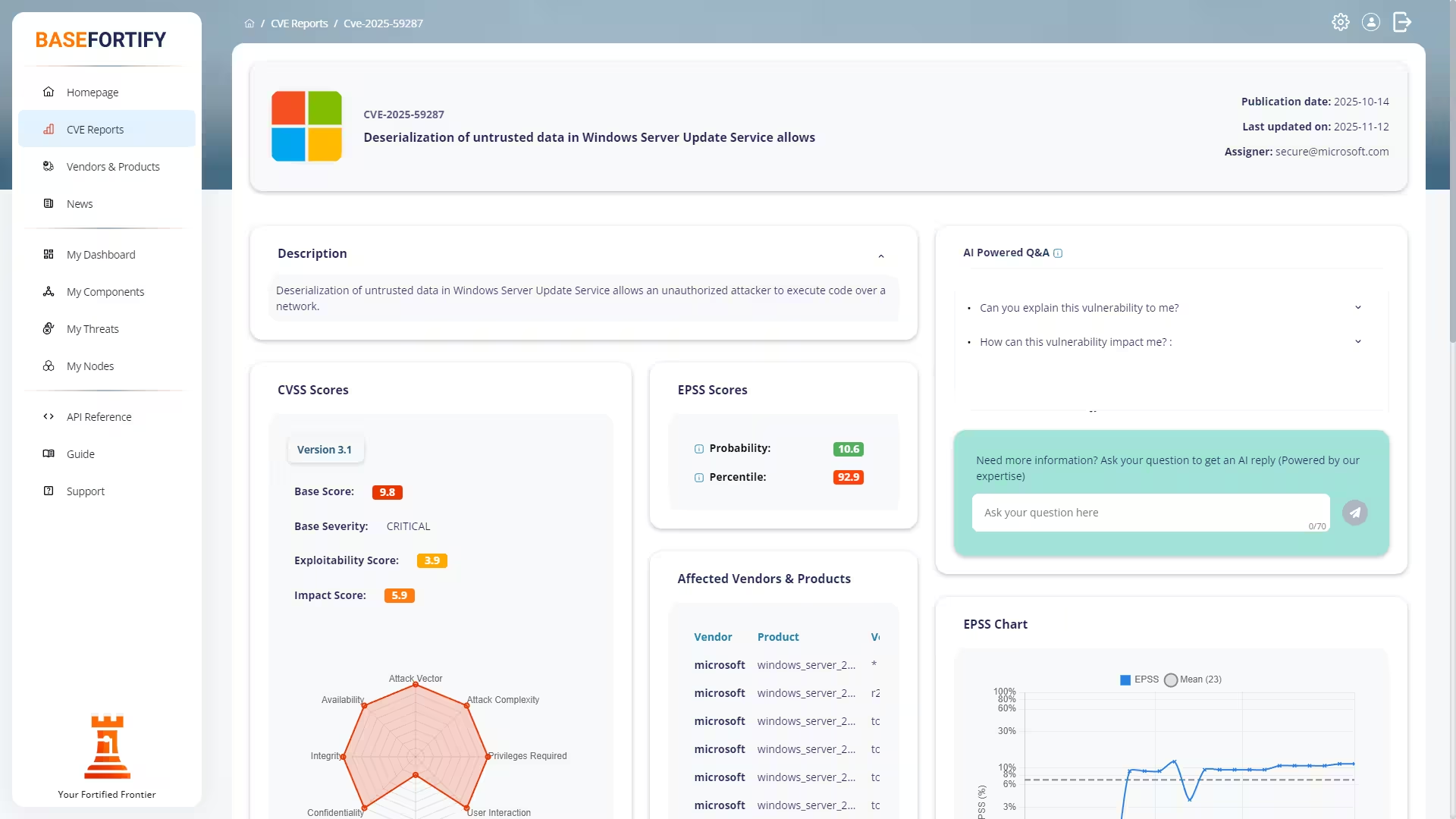
Stay ahead of risks with prioritized vulnerability insights and enriched CVE details. Every report is expanded with context from trusted sources, helping you quickly see what matters and why it matters. With clear formatting and actionable information throughout, you have everything you need to make fast and confident remediation decisions.
Built for Every Environment
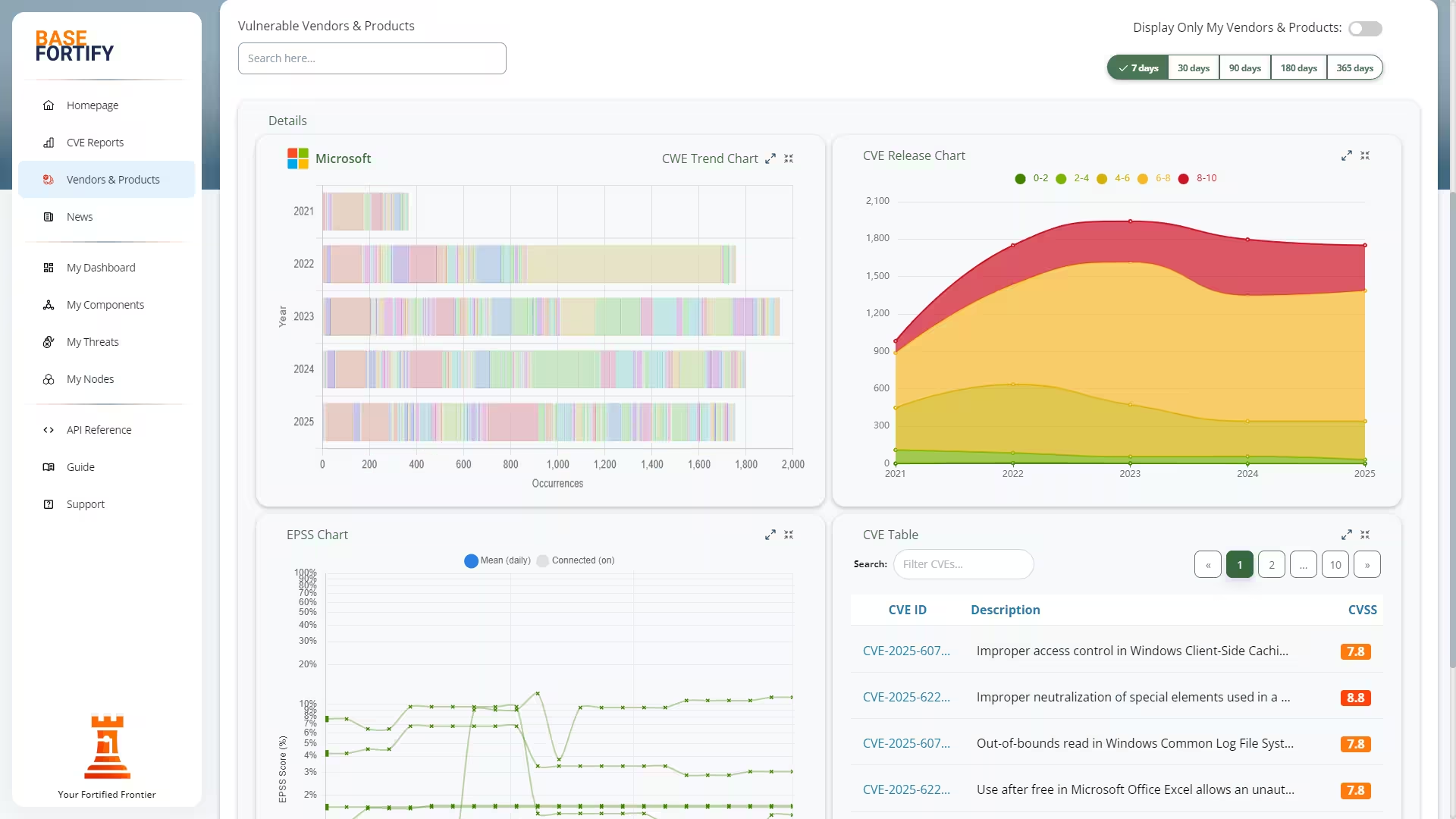
Track vulnerabilities across Windows, Linux, macOS, and virtualised systems with zero deployment overhead. Your nodes report only the essentials, giving you a precise picture of your exposure without scanning or intrusive tools. Whether you manage a small office network or a distributed environment, BaseFortify helps you stay in control with fast, device-specific vulnerability matching.
Threat Intelligence Made Practical
Get rich security context with every CVE you review. Each report includes CVSS scores, CWE classifications, KEV flags, and additional insight to support quick decision-making and remediation planning. Our platform surfaces what matters most, so you can focus on the vulnerabilities that pose real risk to your organisation — not just long lists of identifiers.
Key Features
Powered by trusted sources: MITRE CVE/CWE, FIRST EPSS, CISA KEV — with AI assistance to keep it simple.
Cross-Platform Vulnerability Coverage
- Match your applications, operating systems, and services against known CVEs — no complex scanning or intrusive deployment required.
- Track vulnerabilities consistently across physical, virtualised, cloud-hosted, and mobile environments.
- Supports Windows, Linux, and macOS today, with Android and WordPress coverage coming soon.
Vulnerability Prioritization
- Prioritise vulnerabilities quickly with CVSS severity and EPSS likelihood to see what needs attention first.
- Identify high-risk issues with CISA KEV to understand which vulnerabilities are actively exploited in the wild.
- Focus remediation effort on the items that matter most instead of getting lost in long CVE lists.
Enriched CVE Reports
- Each CVE includes key details from its official references, advisories, and research links.
- Social media and security feeds are checked to highlight early signals or emerging concerns.
- A basic Q&A is generated for every CVE to explain what it is and why it matters.
- A context-aware AI assistant can expand on any report, simplify technical details, and help prepare guidance for others.
Component Management
- Maintain components per node or device, so you always know which software runs where.
- Add components manually with autocomplete to quickly find the right vendor and product.
- Import in bulk by running simple commands on Windows, Linux, or macOS and pasting the output into an intelligent input field.
- Upload full lists of components from CSV or JSON files when working with larger environments.
- Use a visual update panel that compares new and existing lists, so you can approve changes instead of doing manual checks.
- Integrate via REST API if you want components to stay in sync with other systems.
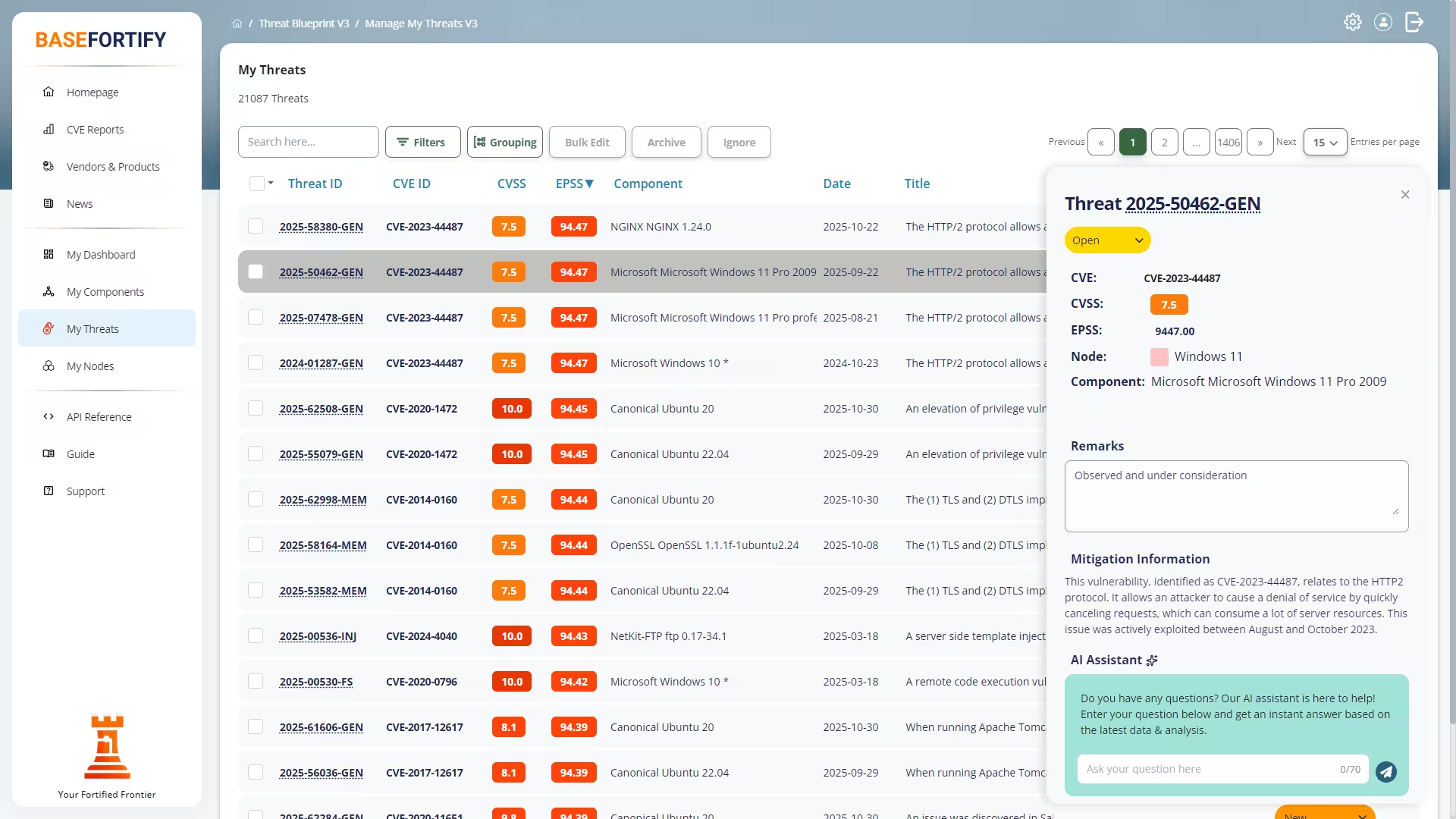
Early-Warning Matches & Threat Status
- CVE reports are annotated with composite CPEs when an official CPE is not yet available.
- These provisional matches receive an early-warning status until the correct CPE is published.
- Each match gets a threat type identifier to show whether it relates to malware, cryptography, configuration issues, or other categories.
- Threats move through a structured remediation workflow to help teams address issues efficiently and consistently.
Remediation Workflow
- Every threat includes a clear, actionable fix — with the AI assistant ready to explain or refine it on demand.
- Handle multiple related vulnerabilities at once with bulk updates when several CVEs impact the same component.
- View threats grouped by component, giving you an instant overview of which systems need attention first.
REST API Integration
- OAuth-secured REST API for safe, controlled access from your own tools and platforms.
- Perform full CRUD operations on nodes, components, and threats to keep data in sync with CMDB, ITSM, or other systems.
- Retrieve enriched CVE and CPE data programmatically to power dashboards, reports, or automation.
- Automate routine updates and checks so vulnerability data flows into existing workflows instead of living in another silo.
Enterprise-Grade Security
- Continuous monitoring and daily security patches keep the platform protected.
- Strong passwords and built-in two-factor authentication secure every login.
- Regular encrypted backups ensure your data remains intact and recoverable.
- All data is stored securely and encrypted with our trusted partner in the Netherlands.
Notifications & Alerts
- Receive new threat notifications by email as soon as they match your environment.
- Set alert thresholds for CVSS severity, EPSS likelihood, and CISA KEV exploitation status.
- Get alerts instantly in Slack or Microsoft Teams to keep your team aligned and responsive.
- Integrate with ServiceNow to feed high-priority vulnerabilities directly into your workflow.
Ready to explore how this fits your environment?
Dashboards & Reporting
- View a real-time dashboard with top threats, recent threats, and priority items ranked by CVSS or EPSS.
- See which components are most affected through an automatically generated Top Components list.
- Understand overall exposure with a threat-status histogram showing progress across lifecycle stages.
- Explore each device using an attack-chain diagram that visualizes how multiple CVEs can be linked during exploitation.
- Attack chains are generated using CWE, CAPEC, and MITRE ATT&CK mappings for clear insight into real-world risks.
Single Sign-On
- Integrate seamlessly into your identity landscape with Single Sign-On (SSO) based on SAML.
- Employees authenticate once through your identity provider — no extra passwords to manage.
- Centralised identity control ensures consistent access policies, fast onboarding, and secure offboarding.
Online Support
- Reach our support team easily for product guidance and cybersecurity or privacy-related questions.
- Use the built-in ticketing system to submit issues, apply tags, and track resolution through transparent statuses.
Deployment & Installation
- No agents, scanners, or complex infrastructure — setup is fast and lightweight.
- Add components manually, import in bulk, or sync automatically through the REST API.
- New users follow an interactive onboarding track supported by the built-in AI assistant.
Data Protection & Privacy
- All customer data is stored securely in the Netherlands and encrypted in transit and at rest.
- Access is restricted to authorised support staff, with intentionally short retention periods.
- GDPR-aligned handling ensures confidentiality, transparency, and full control over your data.
Compliance & Standards
- Runs within an ISO 27001-certified environment for secure operations.
- Developed using OWASP-aligned practices to reduce exposure to common vulnerabilities.
- Meets modern WCAG accessibility standards for a universally accessible interface.
Integrations
Connect your existing tools, identity providers, and infrastructure with seamless, secure integrations. Notifications, identity, and data flows plug into your existing stack instead of forcing you to start over. Below are some of the services we support today, with more being added over time.
Ready to explore how this fits your environment?
Getting started is simple
Three straightforward steps — add your components, see your risks, and start fixing what matters most.
Add your components
Enter components manually, paste command output from your systems, or import lists from CSV or JSON. As soon as they are in, they are matched to official CPEs.
See relevant vulnerabilities
CVEs tied to your stack are surfaced with CVSS, EPSS, and CISA KEV context, so you immediately see which issues are most urgent for your environment.
Act and track progress
Use enriched reports, clear remediation steps, and status tracking on nodes and components to follow work through to completion without spreadsheets.
